On Tuesday, March 26, 2024, Baltimore’s Francis Scott Key Bridge of about 1.6 miles, which had stood strong for nearly 50 years crumbled like a house of cards. The collapse occurred after a massive container ship lost power and collided with one of the bridge support pillars leaving multiple people dead including six construction workers. Also, 64 % of Baltimore County’s small businesses lost revenue due to the Key Bridge collapse.
“The Key Bridge did not have any redundancies”, according to Jennifer Homendy, agency Chair of the National Transportation Safety Board (NTSB). This implies that if a part fails, that will likely cause a portion or the entire bridge to collapse. Redundancy is a commonly applied principle for fault tolerance against accidental faults. Do organizations incorporate redundancies in their security services as the potential impacts of failures can be devastating?
Traditionally security services provide guarantees relating to confidentiality, integrity, and availability but in reality, the security attributes are not survivable by implementing a single method. One of the most effective strategies to protect data and maintain continuous operations is through redundancy.
Understanding Resilience in Security Services
Resilience, in the context of IT and cybersecurity, refers to the implementation of additional components, systems or processes to increase reliability, minimize downtime, and maintain business continuity. It can be applied to various aspects of security, including hardware, software, data, and processes. By incorporating redundant systems, organizations can ensure that their security services remain operational even in the face of unexpected disruptions or attacks.
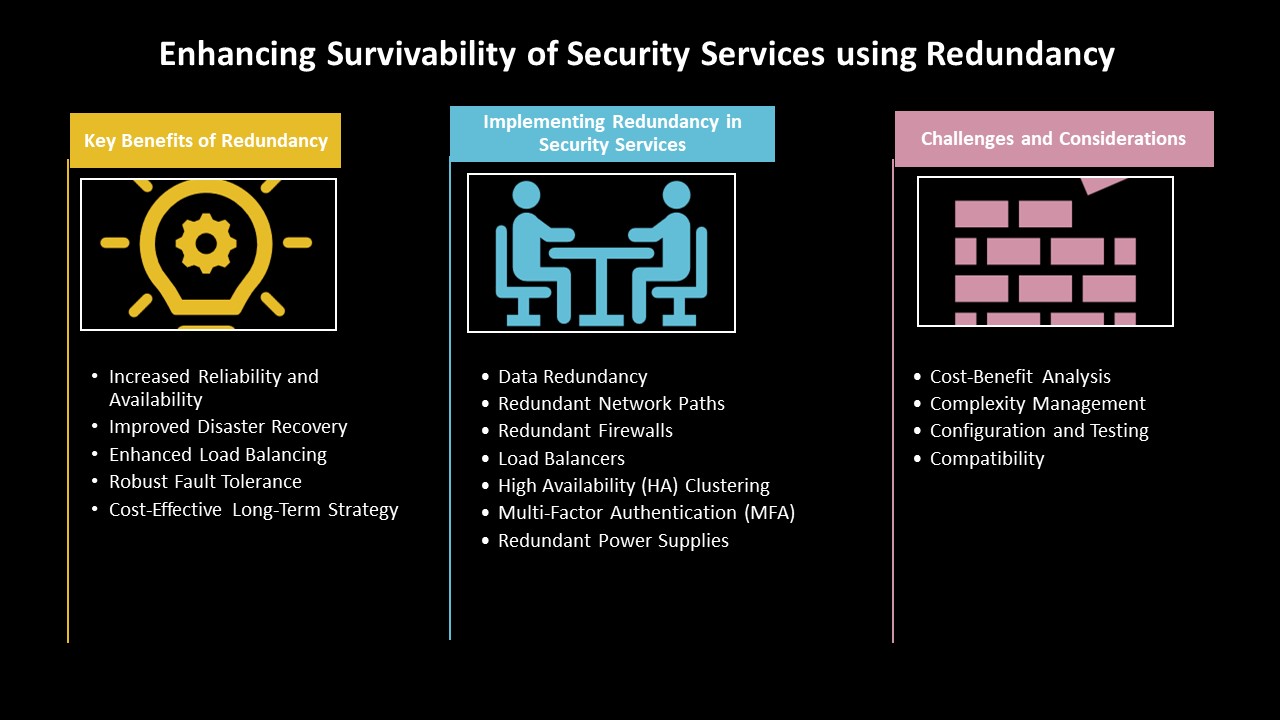
Key Benefits of Resilience
Increased Reliability and Availability: Redundancy significantly boosts the reliability and availability of security services. Having multiple systems or components in place ensures that if one component fails, another can seamlessly take over, minimizing downtime and maintaining continuous protection.
Improved Disaster Recovery: By having backup systems in place, organizations can swiftly switch to redundant components in the event of a failure, minimizing service disruptions and maintaining business continuity.
Enhanced Load Balancing: Redundancy can also aid in distributing workloads across multiple systems, preventing any single component from becoming a bottleneck and enhancing overall performance.
Robust Fault Tolerance: Redundancy adds layers of fault tolerance, enabling systems to continue functioning correctly despite the failure of individual components.
Cost-Effective Long-Term Strategy: While implementing redundancy may involve upfront costs, it is a cost-effective strategy in the long run. The potential losses from security service failures, such as data breaches, downtime, and reputational damage, far outweigh the investment in redundant systems.
Implementing Resilience in Security Services
Data Redundancy: Regularly backing up data and maintaining replicated databases in different offsite locations ensure that data is not lost and can be restored in the case of corruption or failure. Utilizing cloud services for backup can add an extra layer of security and accessibility.
Redundant Network Paths: Network redundancy involves creating multiple pathways for data to travel within an organization’s network. By establishing multiple network paths, single points of failure can be prevented. If one network path becomes unavailable due to an attack or failure, traffic can be rerouted through an alternate path, maintaining network availability and performance.
Redundant Firewalls: Firewalls are critical components of network security. Deploying firewalls in active-active (both firewalls actively handle traffic) or active-passive (one firewall is active while the other is on standby) configurations ensures continuous protection even if one firewall fails.
Load Balancers: Deploying load balancers can distribute incoming traffic across multiple servers, ensuring no single server becomes overwhelmed. This not only improves performance but also adds redundancy, as traffic can be redirected to healthy servers if one server fails.
High Availability (HA) Clustering: Implementing HA clustering involves grouping multiple servers so that if one server fails, another server in the cluster can take over its functions without interruption. This is particularly useful for critical applications and services that must remain operational at all times.
Multi-Factor Authentication (MFA): Implementing MFA with redundant authentication methods ensures that even if one authentication factor is compromised, additional factors provide continued security, reducing the risk of unauthorized access.
Redundant Power Supplies: Ensuring redundant power supplies and uninterruptible power supplies (UPS) can keep security systems operational during power outages, maintaining protection and availability.
Challenges and Considerations
While resilience offers significant benefits, it is not without challenges. Organizations must carefully plan and implement resilience to avoid unnecessary complexity and costs. Key considerations include:
Cost-Benefit Analysis: Implementing redundant systems can be expensive, requiring additional hardware, software, and maintenance efforts. Weigh the costs of implementing redundancy against the potential risks and impacts of service failures.
Complexity Management: Managing redundant systems can add complexity to the IT infrastructure, requiring advanced skills and expertise. Hence, avoid excessive complexity that can arise from managing multiple redundant systems.
Configuration and Testing: Proper configuration and regular testing of redundant systems are crucial to ensure they function correctly during an actual failure or attack. Continuously test redundant systems to ensure they function as expected during a failure.
Compatibility: Ensure compatibility between primary and redundant systems to facilitate seamless failover.
In conclusion, enhancing the survivability of security services through resilience is a powerful strategy against cyber threats. By duplicating critical components and systems, organizations can significantly improve their reliability, availability, and fault tolerance. While resilience requires careful planning and huge investment, the benefits far outweigh the potential risks and costs associated with security service failures. In the face of ever-evolving cyber threats, redundancy stands as a key pillar in the foundation of robust and resilient cybersecurity strategies.