In today’s digital-first world, cybersecurity is no longer the responsibility of just the IT team. It’s a business-wide priority. Whether you’re running a small business or managing a large organization, cyber risks can affect operations, finances, reputation, and customer trust. That’s why taking a lifecycle approach to cybersecurity risk management is essential.
What Is a Lifecycle Approach?
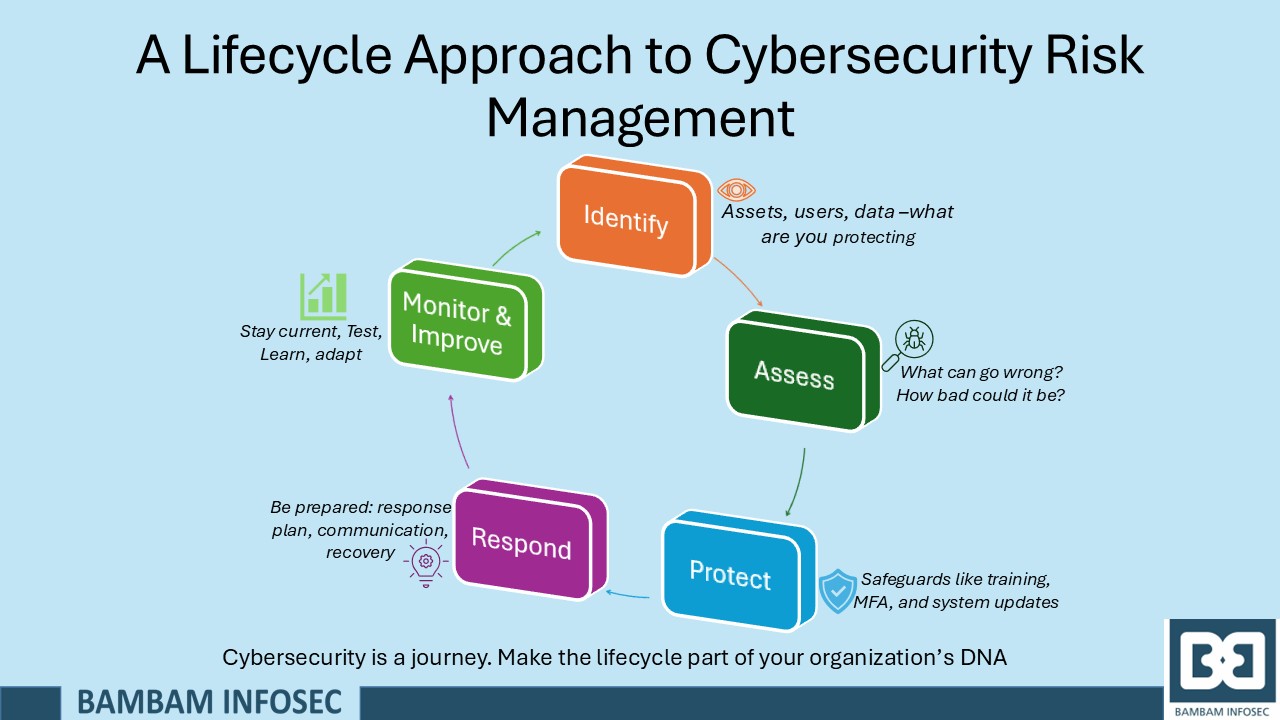
A lifecycle approach means treating cybersecurity not as a one-time project or checklist, but as an ongoing, evolving process. Just like a product goes through stages from design to retirement, cybersecurity should follow a structured, repeatable cycle to identify, assess, respond to, and monitor risks.
The 5 Stages of the Cybersecurity Risk Management Lifecycle
1. Identify – Know What You Need to Protect
Before you can protect something, you need to know what you have. Without this visibility, you’re essentially guarding an invisible target. This stage is about understanding your digital assets—like customer data, financial systems, and communication platforms. It includes:
- Listing critical systems and data
- Understanding how your business uses technology
- Recognizing potential threats and vulnerabilities
This step lays the foundation for smart decision-making.
2. Assess – Understand the Risks
Once you know what’s important, it’s time to evaluate the risks. Ask questions like:
- What could go wrong?
- What threats are out there?
- What are your weak points?
- What would the impact be?
Risk assessment helps you prioritize the most serious threats, so you focus resources where they matter the most.
3. Protect – Build Your Defenses
Now that you understand your risks, you can take action to reduce them. This doesn’t always mean buying expensive tools—it includes:
- Training employees to recognize phishing emails
- Using strong passwords and two-factor authentication
- Keeping software and systems updated
- Limiting who can access sensitive data
Protection isn’t just about tech—it’s about habits and awareness. These everyday practices form the backbone of strong cyber hygiene.
4. Respond – Be Ready for Incidents
Even with the best protection in place, things can go wrong. What matters is how quickly and effectively you respond. A good response plan includes:
- Clear roles and responsibilities
- Steps to contain the damage
- Communication with stakeholders
- Learning from what happened
Being prepared reduces panic, limits damage and builds resilience.
5. Monitor and Improve – Keep Watch and Adapt
Cyber threats are always changing, so cybersecurity must evolve too. Regularly reviewing your systems, testing your defenses, and learning from near-misses or industry trends will help keep your organization a step ahead.
This is the phase where you ask: What’s working? What’s not? What needs to be updated?
Why This Matters
Cybersecurity isn’t a destination—it’s a journey. A lifecycle approach helps organizations:
- Build a culture of awareness
- Make informed, strategic decisions
- Reduce the likelihood and impact of cyber incidents
- Show customers and partners that you take their data seriously
You don’t need to be a technical expert to play a role. Everyone has a part to play—from frontline staff spotting suspicious emails to leadership investing in smart cyber practices.
Final Thoughts
Cyber risk is a reality of modern business—but it doesn’t have to be overwhelming. By adopting a lifecycle approach to cybersecurity risk management, organizations can manage threats proactively, rather than reactively. Think of it like good health: it’s better to build habits that prevent illness than wait until something goes wrong.
Let’s treat cybersecurity not as a problem to solve once, but as a responsibility to manage continuously.