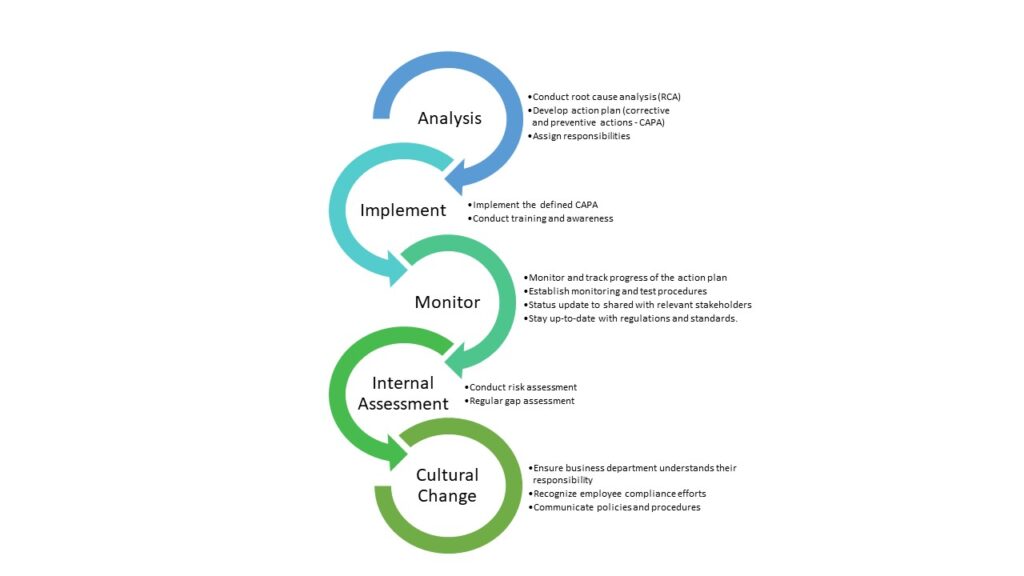
How can recurrence audit findings be prevented?
Organizations must take proactive measures to identify and address any issues identified during an audit to minimize the probability of the recurrence of audit findings.
How can recurrence audit findings be prevented? Read More »