In today’s digital-first environment, managing cybersecurity risk isn’t a one-time exercise—it’s a lifecycle. The NIST Risk Management Framework (RMF) provides a structured, repeatable, and flexible approach to integrating security into every stage of an information system’s life. Adopted by U.S. federal agencies and increasingly embraced by the private sector, the RMF helps organizations embed security into strategy, design, operations, and monitoring.
What Is the NIST RMF?
The RMF, developed by the National Institute of Standards and Technology (NIST) and outlined in Special Publication 800-37, guides organizations through a seven-step process to identify, assess, and manage risk. It aligns with key documents such as FIPS 199, FIPS 200, and NIST SP 800-53, offering a comprehensive approach to security and privacy.
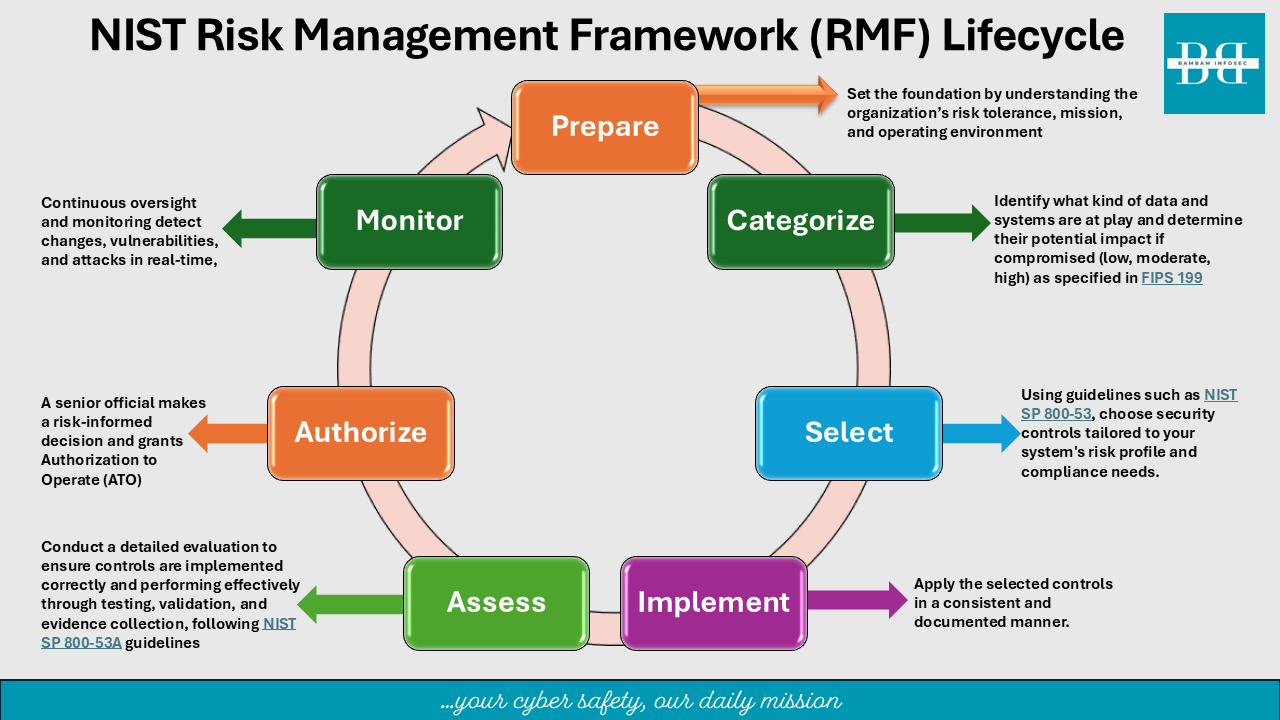
At its core, the RMF consists of seven steps, each representing a phase in the lifecycle of information system risk management and each stage feeds into the next, ensuring continuous risk analysis and mitigation.
The RMF steps are:
1. Prepare
Set the foundation by understanding the organization’s risk tolerance, mission, and operating environment. This step enhances readiness and aligns cybersecurity goals with business objectives.
2. Categorize
Identify what kind of data and systems are at play and determine their potential impact if compromised (low, moderate, high) as specified in FIPS 199. This classification drives the selection of appropriate safeguards.
3. Select
Using guidelines such as NIST SP 800-53, choose security controls tailored to your system’s risk profile and compliance needs. This includes technical, operational, and management controls. It helps avoid both under- and over-protection.
4. Implement
Apply the selected controls in a consistent and documented manner. This is where planning meets execution, and good documentation ensures accountability.
5. Assess
Conduct a detailed evaluation to ensure controls are implemented correctly and performing effectively through testing, validation, and evidence collection, following NIST SP 800-53A guidelines. Independent assessors may be involved to provide objective insight.
6. Authorize
Based on the assessment, a senior official makes a risk-informed decision and grants Authorization to Operate (ATO). This step underscores accountability and transparency.
7. Monitor
Cyber threats evolve rapidly—continuous oversight and monitoring detect changes, vulnerabilities, and attacks in real-time, enabling timely mitigation and system updates. Also, trigger reassessments as needed.
Benefits of the RMF
This lifecycle approach offers several benefits:
- Structured Compliance: Meets federal mandates like FISMA and aligns with broader frameworks like ISO 27001.
- Risk Transparency: Makes risk visible to all stakeholders via documentation and reporting.
- Lifecycle Integration: Embeds risk decisions early in the SDLC (Systems Development Life Cycle).
- Adaptable: Tailors to various organizational sizes and missions.
Real-World Relevance (Government Contractor)
A federal IT contractor deploying a cloud solution for a civilian agency uses the RMF to gain ATO. They categorize their system as “moderate impact,” select baseline controls from NIST 800-53, and perform security control assessments via automated tools and manual testing. Once authorized, they establish a continuous monitoring program with automated dashboards.
Challenges and Considerations
- It can be resource-intensive without automation or team alignment.
- Complexity may slow smaller organizations without RMF experience.
- Tends to be more compliance-focused; pairing with quantitative models like FAIR can add deeper financial insight.
Supporting Tools
- eMASS – Used by the DoD to manage RMF documentation.
- OpenRMF – Open-source tool supporting workflow automation.
- Archer GRC – Commercial platform integrating NIST RMF controls with broader risk governance tools.
Conclusion
The NIST RMF provides more than just a compliance checklist—it’s a comprehensive methodology that embeds cybersecurity into every organizational layer. As risk evolves from a back-office concern to a board-level agenda, frameworks like RMF will remain essential for building secure, resilient, and trustworthy digital environments.