Information security breaches are one of the main challenges for businesses today and this can be of particular concern for companies that process, store, and transmit customers’ sensitive information and personally identifiable information (PII). An information security incident occurs when there is a direct or indirect attack on the confidentiality, integrity, and availability (CIA) of an information asset. Even though organizations have increased their investments towards cybersecurity, security incidents continue to occur. The next question will be how best an organization can prepare and response to security incidents and manage data breaches.
At a strategic level, cybersecurity is both a process and a technology, But in reality, it’s a combination of process, technology and people. In the same vein, incident response is predominantly performed by people, with critical assistance from technology and process. An incident response is a critical security function in an organization that aims to manage incidents promptly and cost effectively. Additionally, incident response teams are perceived as the ‘fire-fighters’ who are responsible for reducing the impact of breaches and supporting the business resume operations as soon as possible.
Best-practice guidelines provide detailed step-by-step procedures and actions to manage incidents (NIST SP 800-61 Revision 3). Typical incident response life cycles consist of five phases: preparation; identification/detection and analysis; containment; eradication and recovery. Few security researchers term the life cycles as a linear incident response framework and propose an Agile Incident Response Framework. The Agile IR Framework incorporates agile principles to break down the process into smaller, more manageable parts which can be prioritized and continuously delivered over shorter iterations.
Incident response and data breach management are initiative-taking measures that help protect customers’ information by ensuring a quick and efficient reaction to security incidents. Through structured planning, swift containment, and continuous improvement, these methods allow organizations to protect sensitive information from exposure, contain threats, minimize the impact of breaches, maintain compliance, and prevent similar incidents in the future.
Key Components of Incident Response and Data Breach Management
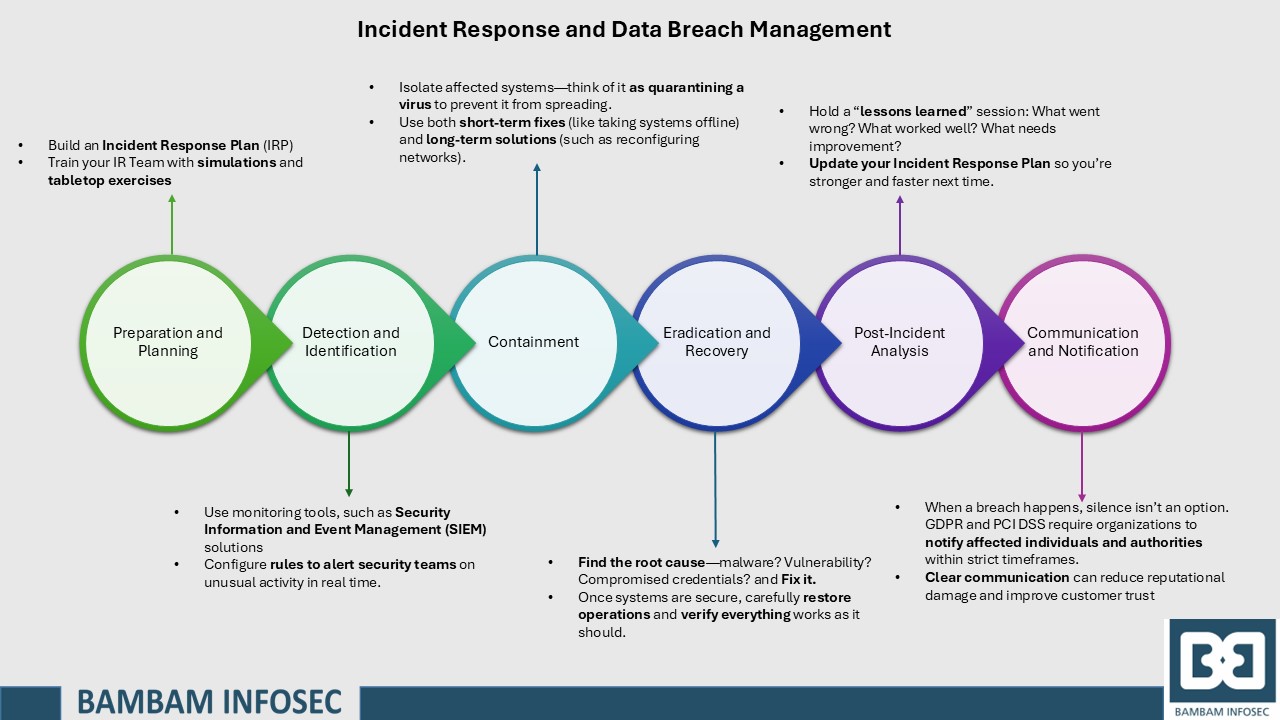
- Preparation and Planning: The foundation of incident response lies in preparation. Organizations must establish an incident response plan (IRP) outlining procedures for detecting, responding to, and recovering from security incidents. This plan includes defining roles and responsibilities, setting up communication channels, and ensuring all staff members are trained in their specific tasks.
- Detection and Identification: Swift detection is essential for effective incident response. Monitoring systems, such as Security Information and Event Management (SIEM) solutions, alert security teams to unusual activity in real time. This early detection helps identify potential breaches before they can fully develop, reducing the likelihood of a full-scale data breach.
- Containment: Once an incident is identified, the containment phase begins. Containment involves isolating affected systems to prevent further data exposure. For example, if a specific server storing cardholder data is compromised, it can be taken offline to stop the spread of the breach. Organizations often have short-term (immediate containment) and long-term (more comprehensive fixes) containment strategies to limit the incident’s impact.
- Eradication and Recovery: After containment, the next step is to remove the root cause of the breach. This may involve removing malicious software, patching vulnerabilities, or strengthening security controls. Recovery ensures that affected systems are restored to normal operation securely. Organizations should assess systems to verify security before they are fully reintegrated into the network.
- Post-Incident Analysis: Following a breach, a post-incident analysis, or “lessons learned” session, allows the organization to review what happened, identify root causes, and implement improvements. This phase is critical for refining security measures and enhancing the incident response plan. It also helps in identifying any additional training or resources needed to better protect cardholder data.
- Communication and Notification: Timely and transparent communication is essential in data breach management. Regulatory requirements like the GDPR and PCI DSS mandate that organizations notify affected individuals and relevant authorities within a specific timeframe. Clear communication can reduce reputational damage and improve customer trust, as stakeholders are kept informed about actions taken to resolve the breach.
Benefits of Incident Response and Data Breach Management for Cardholder Data Security
- Rapid Threat Containment: By responding quickly, organizations can stop a breach before it escalates, reducing the amount of cardholder data that may be exposed. (“Essential Security Methods for Protecting Cardholder Information”)
- Improved Preparedness: Regular testing of incident response plans (e.g., through simulations or tabletop exercises) ensures that security teams are ready to oversee actual incidents effectively.
- Enhanced Compliance: Effective incident response and data breach management are core requirements of security standards like PCI DSS, which mandates organizations to have a defined process for responding to and reporting incidents involving cardholder data.
- Continual Improvement: Each incident response contributes to a stronger security posture, as organizations learn from each incident and improve their strategies to avoid similar future incidents.