Statistics on Financial and Reputational Impact
During the last few decades, the payment industry has grown. There has been a rapid embrace of new technologies in processing customers’ digital transactions. It is essential to secure cardholder information as consumers increasingly rely on online shopping, mobile payments, and digital banking for everyday transactions. Total transaction value in the Digital Payments market is projected to reach US$11.55tn in 2024. This figure is expected to continue climbing as consumers and businesses embrace online commerce. However, this growth can be paralyzed by an alarming rise in cybercrime. According to Cybersecurity Ventures, cybercrime is projected to cost the global economy $10.5 trillion annually by 2025, with a significant portion attributed to data breaches involving sensitive financial information. For consumers, these breaches can lead to identity theft, financial losses, and long-term credit impacts. For businesses, they result in direct financial losses, legal repercussions, and reputational damage that can be difficult to recover from.
To safeguard cardholder data, the Payment Card Industry Data Security Standard (PCI DSS) provides a globally recognized framework to help businesses protect cardholder information by implementing measures like encryption, strong access controls, and regular security testing. Compliance with PCI DSS is required for any organization handling card data, from large retailers to small businesses. A report by Verizon’s 2022 Payment Security Report found that organizations in full compliance with PCI DSS had a 50% lower likelihood of a data breach. Yet, only 43.4% of global organizations were fully PCI DSS compliant, underscoring a critical gap in the widespread adoption of these protective standards.
Incident of Data Breaches
- Marriott International (2022):
Marriott suffered a breach in 2022 that affected the payment and personal information of up to 500 million guests over a four-year period. Hackers accessed the Starwood guest reservation database, exposing payment data, passport information, and contact details. Marriott faced significant legal repercussions and brand damage, leading to regulatory fines totaling $23.8 million. This case highlights the importance of monitoring and securing third-party data sources as outlined by PCI DSS, as well as the severe impact on brand reputation and trust.
- British Airways (2018):
In 2018, British Airways suffered a breach that exposed the payment details of nearly 400,000 customers. Hackers managed to infiltrate the airline’s payment systems and extract card information, which led to fines totaling £20 million by the UK’s Information Commissioner’s Office (ICO). The breach was attributed to insufficient data protection practices, and failure to adequately monitor access points, both areas covered by PCI DSS requirements. Besides the financial penalties, the airline suffered from diminished consumer trust, further impacting its revenue during a time when the airline industry was already under pressure. British Airways’ incident serves as a reminder that proactive monitoring and stringent security practices are essential to protect against evolving cyber threats.
- Equifax (2017):
In 2017, Equifax, a leading credit reporting agency, experienced a data breach that exposed the personal information, including payment card details, of 147 million individuals. The breach was traced to a vulnerability in an open-source web application, a gap that could have been mitigated by regular security patching and vulnerability management, as stipulated by PCI DSS. Equifax eventually agreed to a $575 million settlement to cover costs related to the breach. This case illustrated how neglecting even minor vulnerabilities can lead to massive data exposure and financial loss.
- Home Depot (2014):
Another major breach occurred in 2014 when Home Depot’s POS systems were compromised, exposing 56 million customer credit and debit card records. Hackers used stolen credentials from a third-party vendor to access the network, an incident that could have been mitigated by stricter network segmentation and PCI DSS compliance. This breach cost Home Depot approximately $179 million in settlements and legal fees. In addition, the company faced significant reputational damage and was forced to overhaul its security systems. The incident illustrated the importance of restricting third-party access and implementing network segmentation, as required by PCI DSS.
- Target (2013):
The 2013 Target data breach remains one of the most notorious examples of a failure to secure cardholder information adequately. Hackers exploited a vulnerability in a third-party vendor’s security system to gain access to Target’s network, ultimately installing malware on point-of-sale (POS) systems across stores nationwide. The breach compromised the credit and debit card details of over 40 million customers and resulted in more than $202 million in direct costs to Target, including a $18.5 million settlement with 47 states. The breach led to widespread public backlash and diminished consumer trust, underscoring the need for robust third-party security protocols and strict adherence to PCI DSS standards.
- Heartland Payment Systems (2008):
One of the earliest and most significant breaches that occurred in 2008 was when Heartland Payment Systems, a major credit card processing company, was hacked. Cybercriminals installed malware on the company’s network, which allowed them to steal over 130 million card numbers. The breach led to Heartland paying around $145 million in fines, compensation, and legal fees. In response, Heartland became an advocate for data security, but the damage to its reputation was lasting, with a substantial loss of client trust. This case underscores the critical nature of continuous monitoring, PCI DSS compliance, and proactive malware defenses.
Statistics on Financial and Reputational Impact
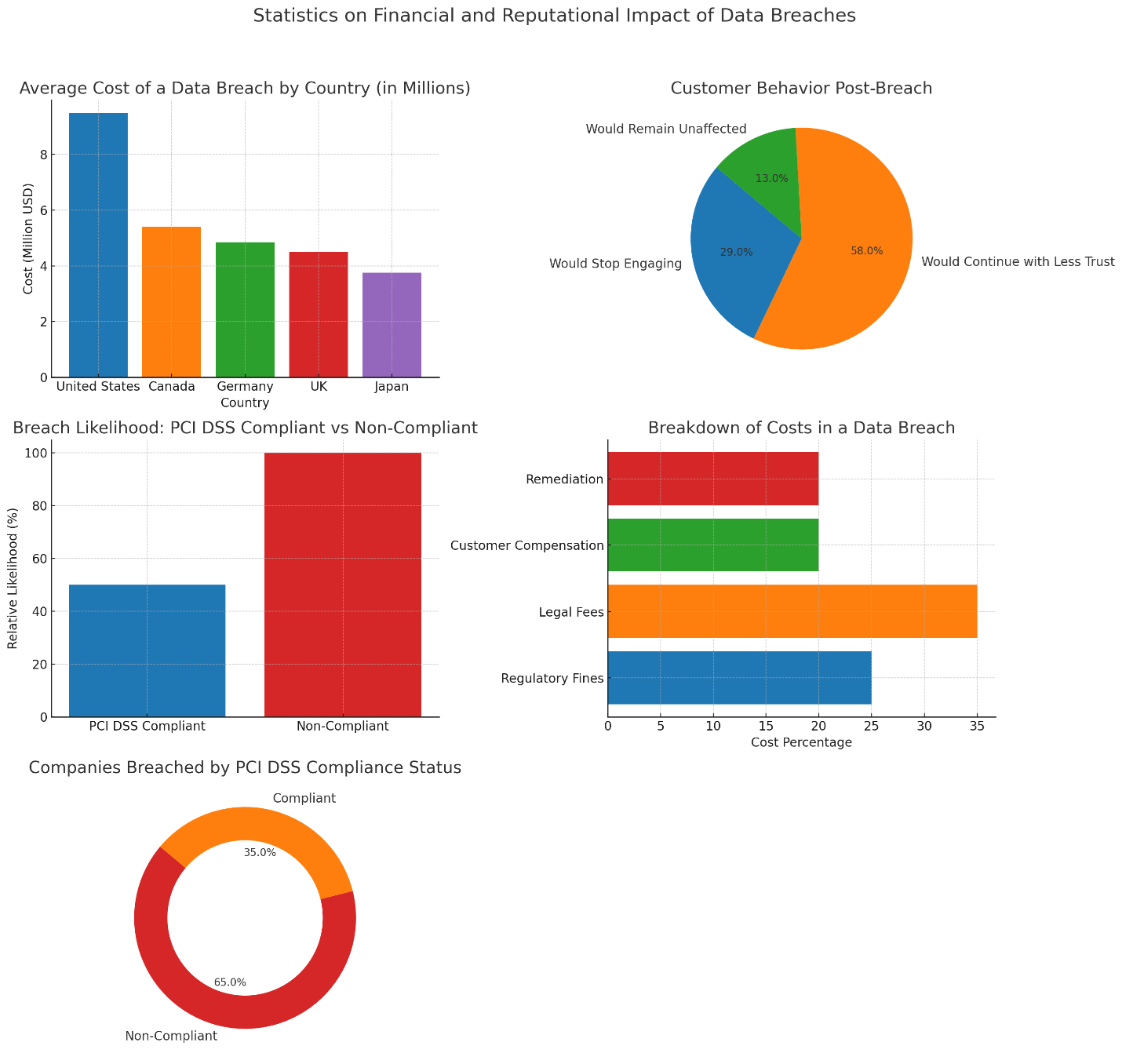
- Financial Impact: According to IBM’s Cost of a Data Breach Report 2023, the global average cost of a data breach has risen to $4.45 million. In the United States, that figure climbs to $9.48 million, with financial institutions facing among the highest costs due to the sensitive nature of cardholder data. These expenses include regulatory fines, legal fees, customer compensation, and the cost of implementing additional security measures post-breach.
- Reputational Damage: Following data breaches, 31% of consumers said they would discontinue their relationship with the breached entity following a data breach, while 65% said they lost trust in the organization after being affected by one or more breaches according to the 2017 Ponemon Institute Study. This erosion of trust has long-term effects on customer loyalty and retention, directly impacting revenue.
- Compliance vs. Non-Compliance: Verizon’s Payment Security Report noted that companies that adhere strictly to PCI DSS compliance are 50% less likely to suffer a data breach. Also, 65% of companies that were breached were found to be non-compliant with PCI DSS, according to the 2022 Ponemon Institute Study on Compliance. This underscores the value of proactive security measures in reducing both the frequency and impact of cyber incidents.
Conclusion:
As these cases and statistics reveal, there are severe financial and reputational consequences of failing to secure cardholder data. PCI DSS is not about compliance but about protecting customers and business integrity. PCI DSS compliance, though rigorous, provides a vital defense against data breaches by implementing encryption, access controls, and continuous monitoring. By investing in robust security practices and adhering to this standard, organizations can significantly reduce their risk of data breaches, build trust with customers, and avoid substantial financial penalties.